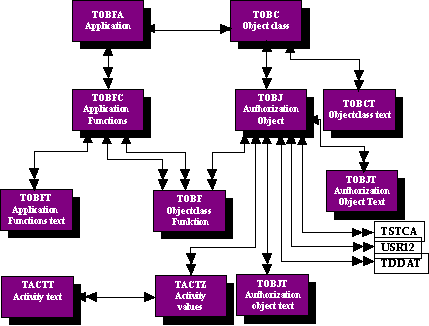
To understand the R/3 Authorization System, from a technical IT point of view, it is important to understand the
Entity-Relation diagram, which can not be found in the R/3 documentation. On this page you will find the diagram for
R/3 2.2F.

An Entity-chart for authorization-checks is nice to have when you are about to plan (or document) which authorizations should be implemented. The entity-chart is especially useful if you want to develop your own utility-applications in Abap/4.
In the R/3 system the traditional tools of the relational database designer/administrator is not used. Neither cascade-deletes nor restrictions are possible, and it is difficult to determine relations and cardinalities from the information provided by the data-dictionary. We are therefore unable to illustrate whether a relation is needed or not. Analyzing table-content shows that some tables are consistently complementary, but this is not always the case.
The reason for this non-application of relational database design principles in the R3 system stems from "sins of the past", i.e. the use of so-called "logical databases". These were implemented as ABAP/4 programs and they are structurally similar to hierarchic databases such as the IMS/DB.
The tables shown contains the data delivered by SAP AG, that need not be modified by the Database Administrator, but must be included in the analysis and implementation of authorizations.
In particular two of the tables shown are of interest :
Note however, that the CO- and PS-modules does not use TACTZ - in CO hypertext is used, and in PS, the values are hardcoded in an ABAP/4 include file. This has been improved substantially with the R/3 3.0 release, so that now 95% of referenced activities are included in TACTZ.
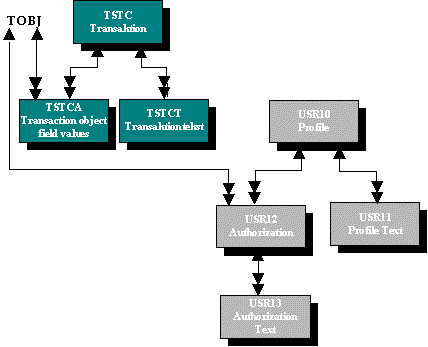
This group envelops the tables that the authorization administrator must primarily customize. TSTC, TSTCA and TSTCT contains authorization-checks controlling access to transactions. These checks are performed automatically by the R/3 system whenever a transaction is called via the R/3 menu or via the command-line.
The remaining tables in this group contains operational authorizations. Authorization objects controls access to perform specific functions in the R/3 system, such as Create, Modify, Delete et.c. Access can be limited to one or more company-codes, accounts, business-areas and so on. Authorizations are bundled in individual profiles, describing the access-level of a single user. Profiles can again be bundled in composite profiles. Users can be assigned both individual profiles and composite profiles.
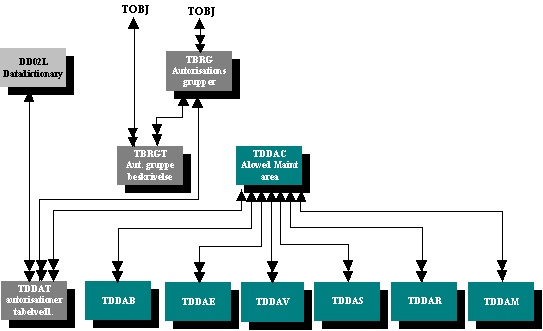
This group of tables contains specialized authorization-checks, which can be customized in the R/3 system - table-authorization to control access to the common table-maintenance function (transaction SM31) and authorization at the field level among others. In this group the tables containing authorization for table maintenance - TBRG, TBRGT and TDDAT - are the most widely used.